Chapter 1
These series of blogs will act as a note-taking environment for me but also as a walkthroogh for the Practical Malware Analysis Book.
Let’s start off with the first labs.
Lab 1-1
The following block represents the exact assignment from the book:
This lab uses the files Lab01-01.exe and Lab01-01.dll. Use the tools and techniques described in the chapter to gain information about the files and answer the questions below.
Questions
1.Upload the files to http://www.VirusTotal.com/ and view the reports. Does either file match any existing antivirus signatures?
In order to calculate the hash of the file, we will use the powershell Get-FileHash command:
Get-FileHash
[-Path] <String[]>
[[-Algorithm] <String>]
[<CommonParameters>]
Applied to our case, the command (run in cmd) will be :
powershell Get-FileHash -algorithm md5 Lab01-01.dll
for the md5 hash, and:
powershell Get-FileHash -algorithm SHA256 Lab01-01.dll
for sha256.
Using the above mentioned information, the hashes for the files are as follows:
Lab01-01.dll
MD5: 290934C61DE9176AD682FFDD65F0A669
SHA256: F50E42C8DFAAB649BDE0398867E930B86C2A599E8DB83B8260393082268F2DBA
Lab01-01.exe
MD5: BB7425B82141A1C0F7D60E5106676BB1
SHA256: 58898BD42C5BD3BF9B1389F0EEE5B39CD59180E8370EB9EA838A0B327BD6FE47
Now, let’s get back to our questions.
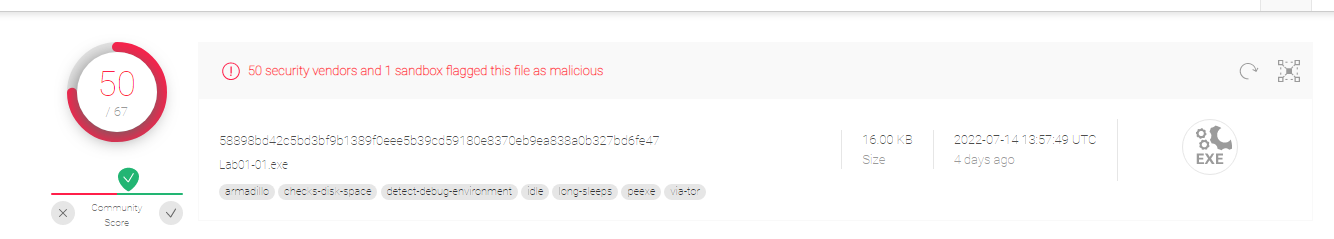
Yes, both of the files match the existing antivirus signatures
The result for Lab01-01.exe:
2.When were these files compiled?
In order to answer this question, we can use two methods:
- We can either check the information from the details tab on VirusTotal, the History section, for the “Creation Time”.
- Or, we can check the IMAGE_FILE_HEADER in PEview and look for the Time Date Stamp:
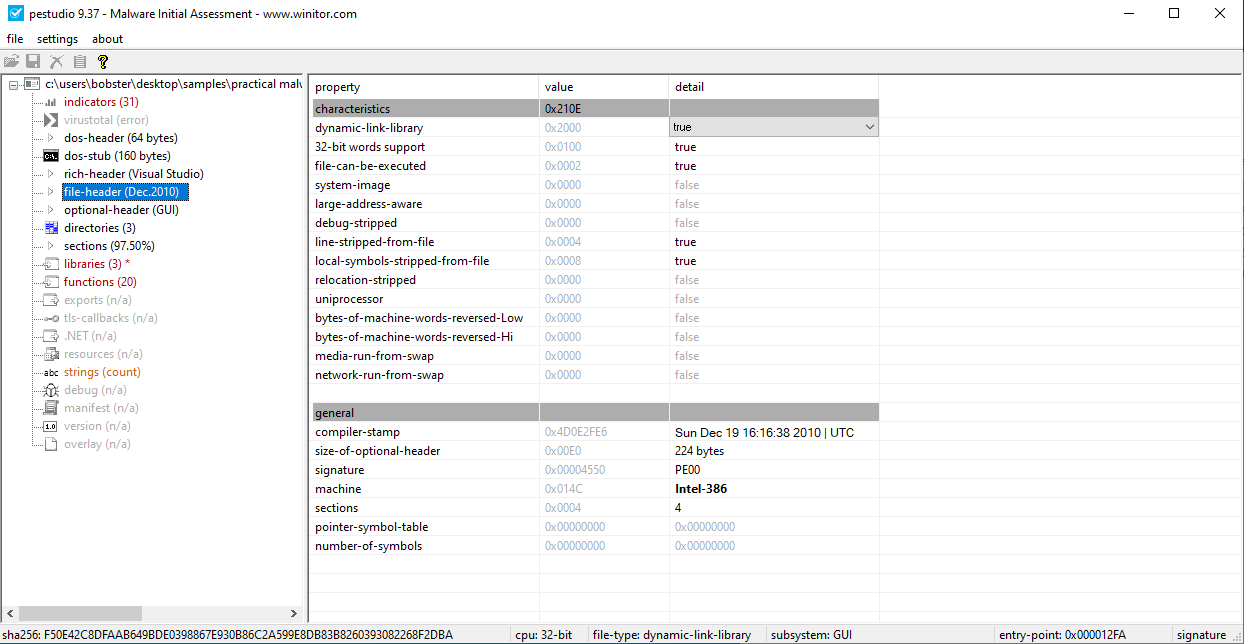
For Lab01-01.dll, the creation time is : 2010/12/19 Sun 16:16:38 UTC
For Lab01-01.exe, the creation time is : 2010/12/19 Sun 16:16:19 UTC
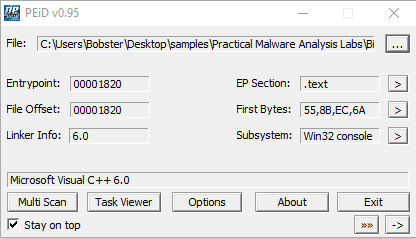
3.Are there any indications that either of these files is packed or obfuscated? If so, what are these indicators?
No, there are not any indicators that either of those files are packed or obfuscated.
As it can be seen in the PEiD, both of them are compiled using Microsoft Visual C++ 6.0 DLL.
4.Do any imports hint at what this malware does? If so, which imports are they?
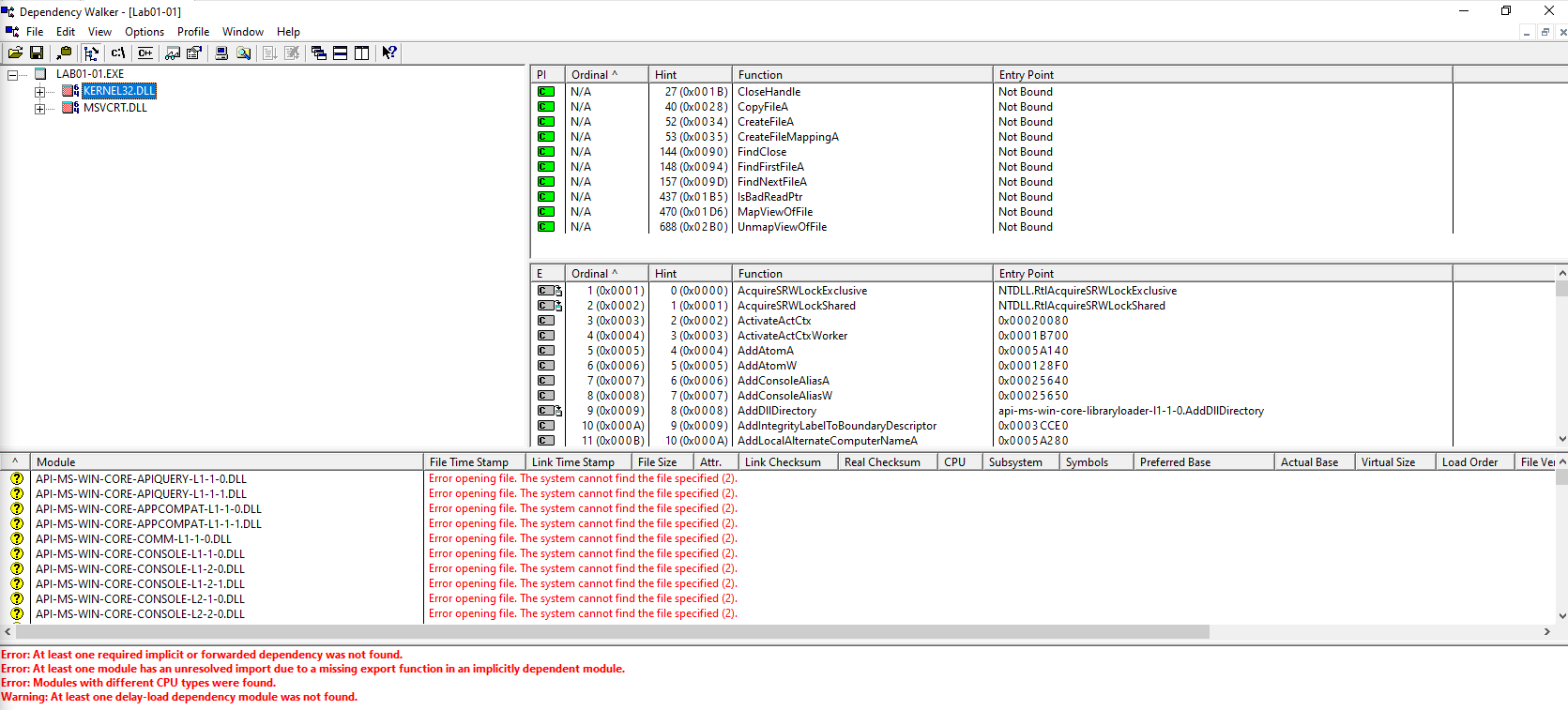
Lab01-01.dll
Taking into consideration that the functions CloseHandle, CreateMutexA, CreateProcessA, OpenMutexA and Sleep are imported from KERNEL32.DLL, we can assume that the .dll will start a process, and sleep (pause its execution) for a certain amount of time, most likely as an evasive measure.
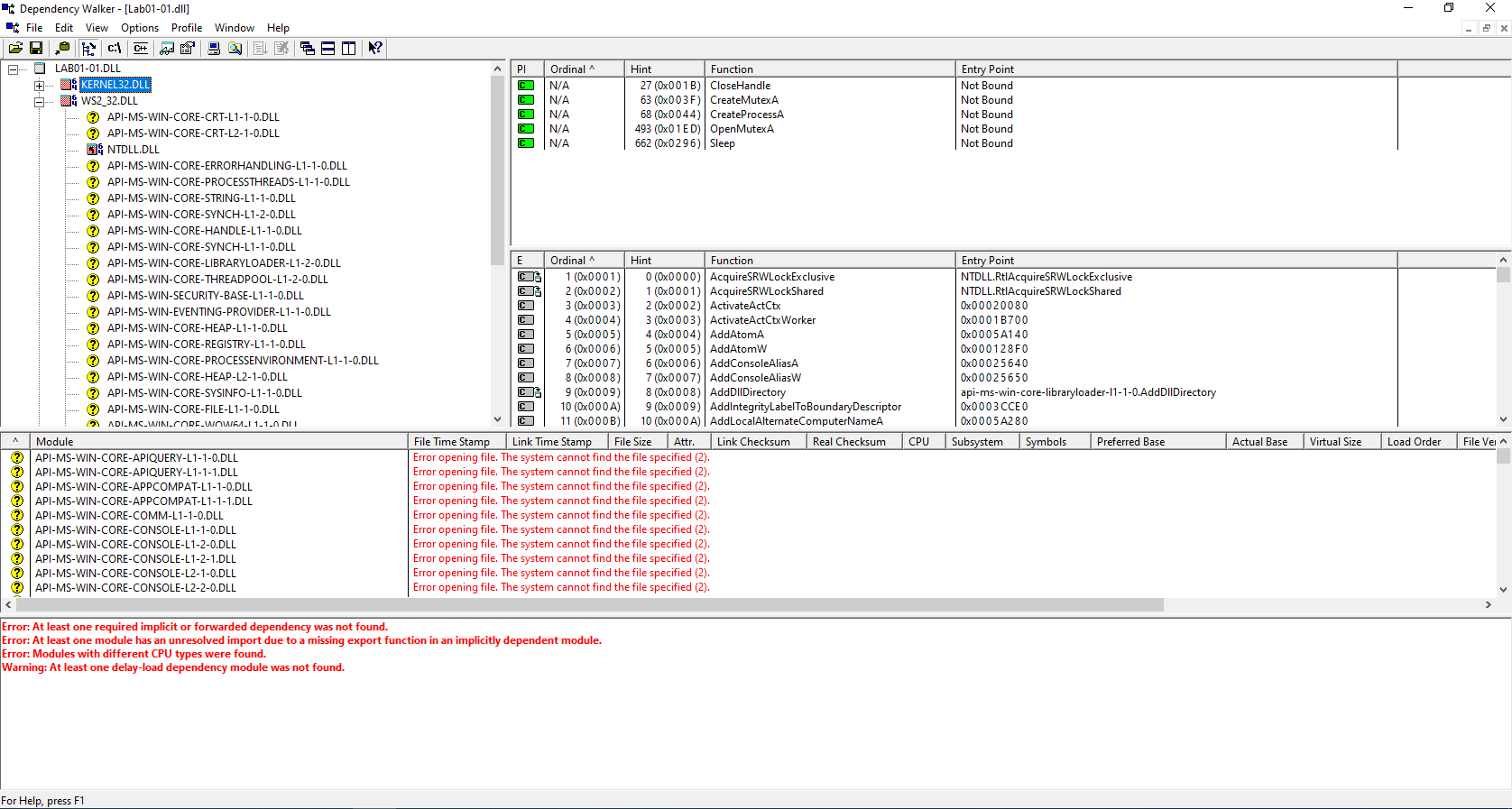
Also, finding the IP address : 127.26.152.13, and the socket specific functions, such as connect,bind imported from WS2_32.DLL led us into thinking that it might connect to a C2 server in order to receive further commands, or to download other malware.
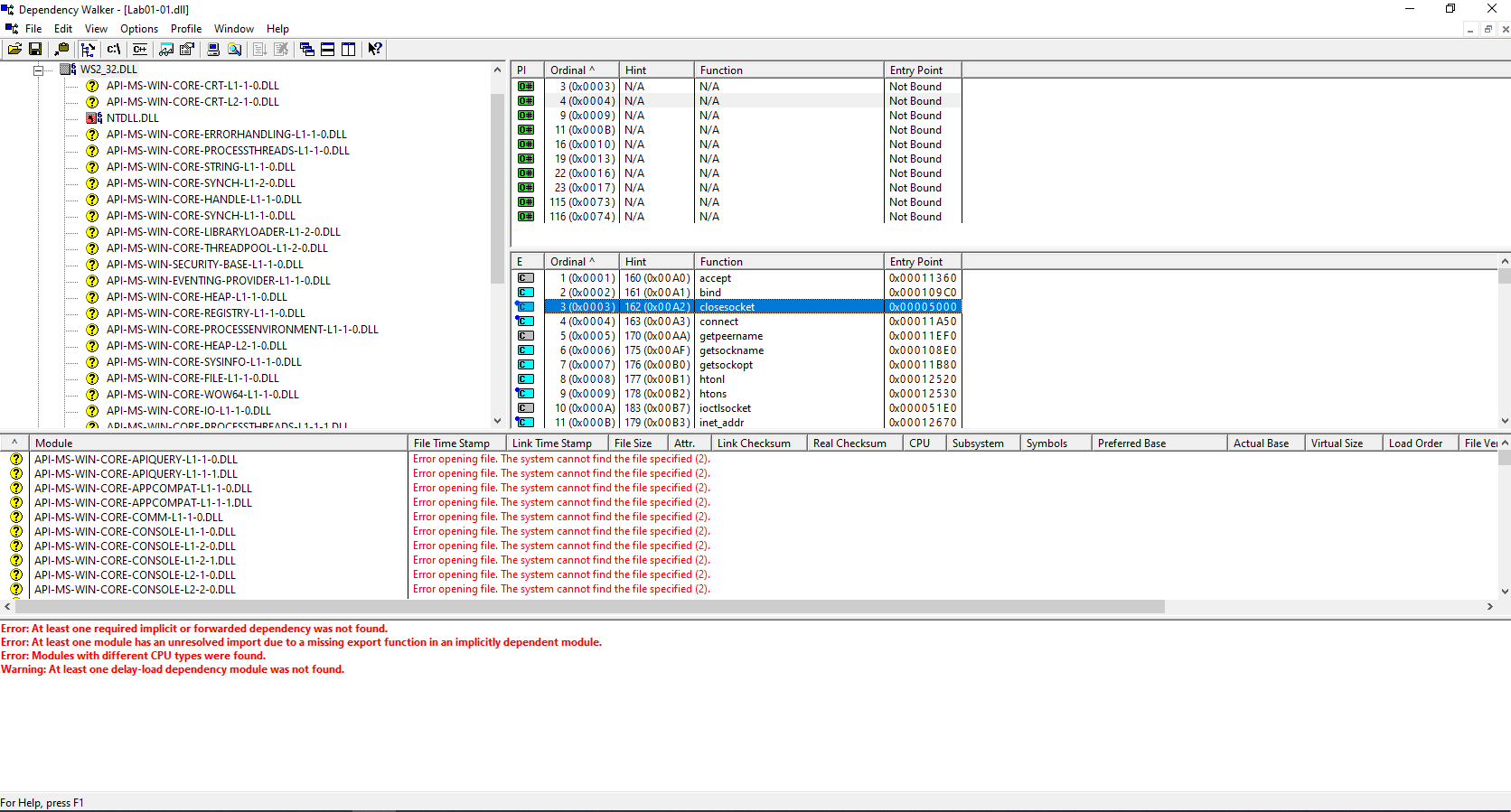
Lab01-01.exe
The .exe imports functions such as FindNextFileA, FindFirstFileA, CreateFile, CopyFile, indicate that the malware will search for specific files and also create and copy some of those.
5.Are there any other files or host-based indicators that you could look for on infected systems?
Yes. If we look inside the **Lab0101.exe** file, we find the string _C:\windows\system32\kerne132.dll which is an attempt to trick the user into thinking that it is the same with Kernel32.
6.What network-based indicators could be used to find this malware on infected machines?
The IP address 127.26.152.13 found in the .dll can be an indicator to find this malware on infected machines.
7.What would you guess is the purpose of these files?
The purpose of the .exe file is to find and run the .dll file, which in turn connects to the C2 server at 127.26.152.13. From there, malicious files can be downloaded.
Lab 1-2
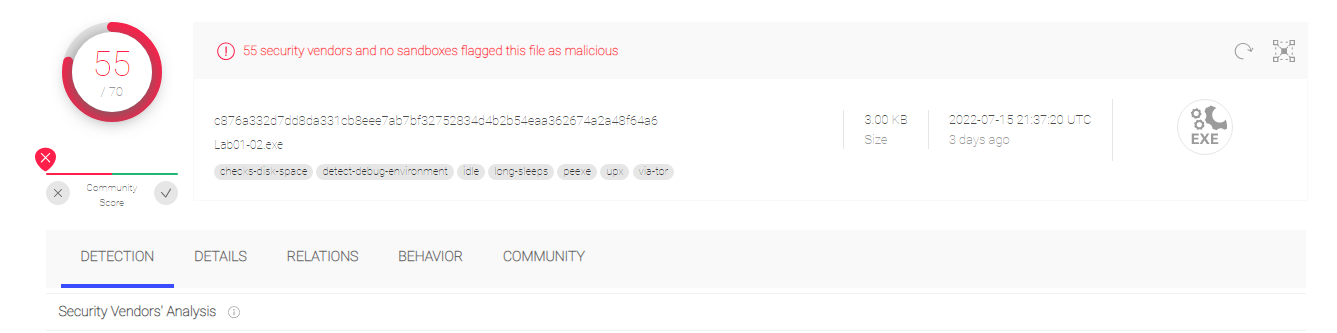
1.Upload the Lab01-02.exe file to http://www.VirusTotal.com/. Does it match any existing antivirus definitions?
Yes, it does. 55 vendors flagged this file as malicious.
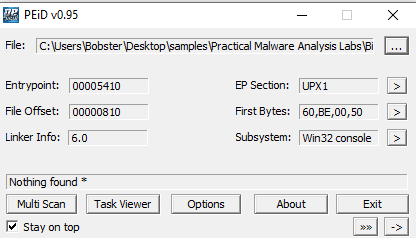
2.Are there any indications that this file is packed or obfuscated? If so, what are these indicators? If the file is packed, unpack it if possible.
As it can be seen in PEiD, the entry point is UPX1. And, recalling the information in the book, the UPX packer changes the name of the sections in such strings.
The .UPX0 section has a raw size of 2048 bytes and a virtual size of 24756 bytes, which indicates that a packer will unpack the executable code to the allocated .text section.
![PeStudio_Lab01-02sections]PeStudio_Lab01-02_sections
So, observing the _UPX0, UPX1, UPX2 sections, we can surely say that the file is packed with the open-source UPX packer.
To unpack it, we can download the UPX tool from github.
Now, let’s run the unpacker:
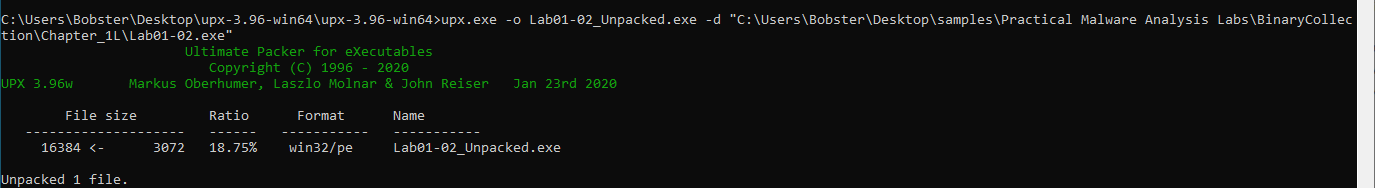
After the unpacking process, we run PeID again and find that this file was compiled using Microsoft Visual C++ 6.0.
Opening the file in PEStudio, we find a lot more informations about the file’s strings and imports.
3.Do any imports hint at this program’s functionality? If so, which imports are they and what do they tell you?
The imports that are visible are:
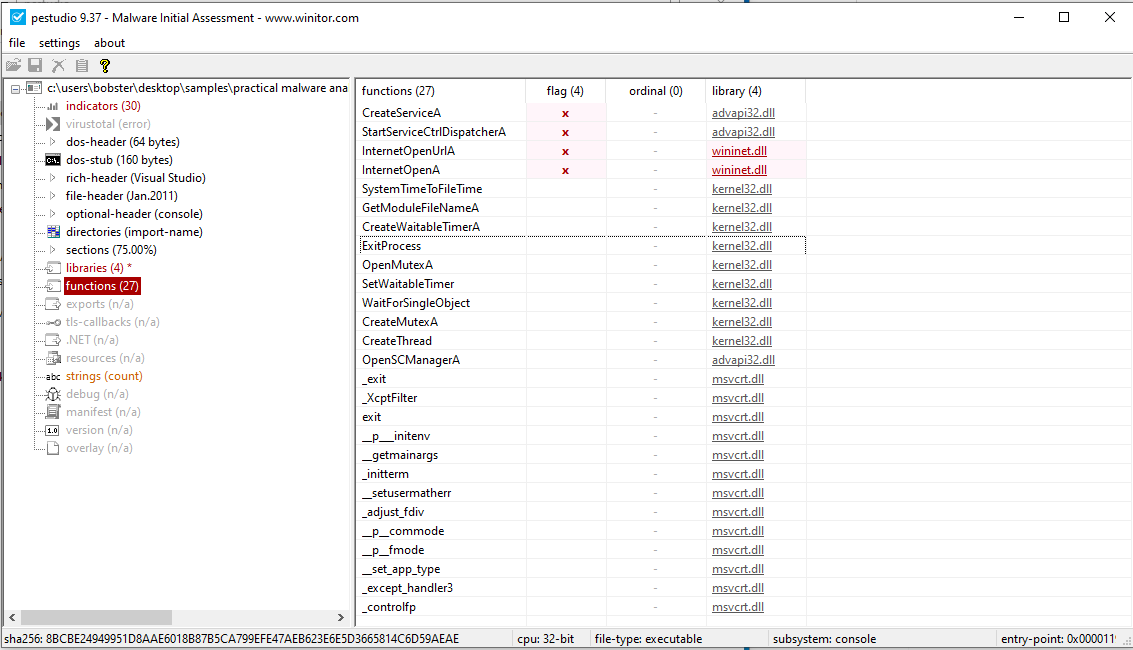
We can assume that the malicious file will try to connect to the http://www.malwareanalysisbook.com URL and bind it to a serice in order to maintain persistence. This might be a way to connect to the C2 server in order to receive further commands or download other malicious files.
4.What host- or network-based indicators could be used to identify this malware on infected machines?
In order to identify this malware on infected machines, we can look for a running service named MalService and also check for connections to the URL http://www.malwareanalysisbook.com .
Lab 1-3
1.Upload the Lab01-03.exe file to http://www.VirusTotal.com/. Does it match any existing antivirus definitions?
As it can be seen, the files matches 62 of the existing antivirus definitions.
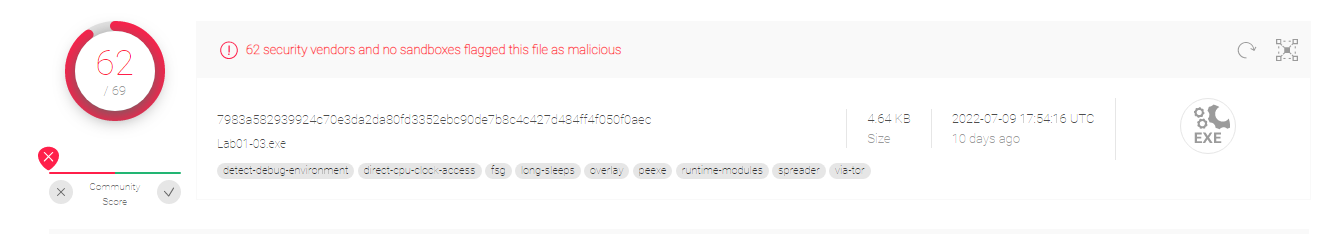
2.Are there any indications that this file is packed or obfuscated? If so, what are these indicators? If the file is packed, unpack it if possible.
PEiD lets us know that FSG 1.0 packer was used for this file.
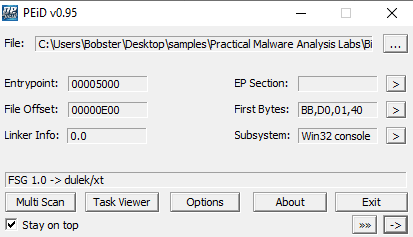
Also, the virtual size of 20480 bytes is way larger than the raw size of 1164 bytes.
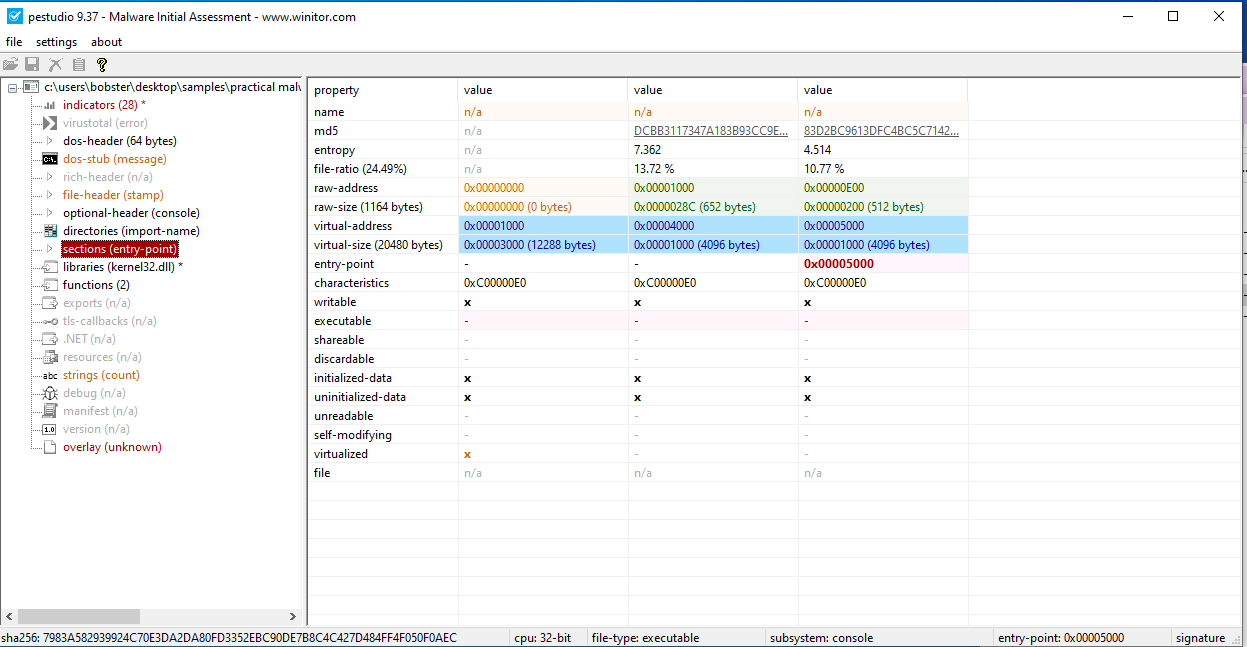
3.Do any imports hint at this program’s functionality? If so, which imports are they and what do they tell you?
The only imports that we can find in this file are LoadLibraryA and GetProcAddress.
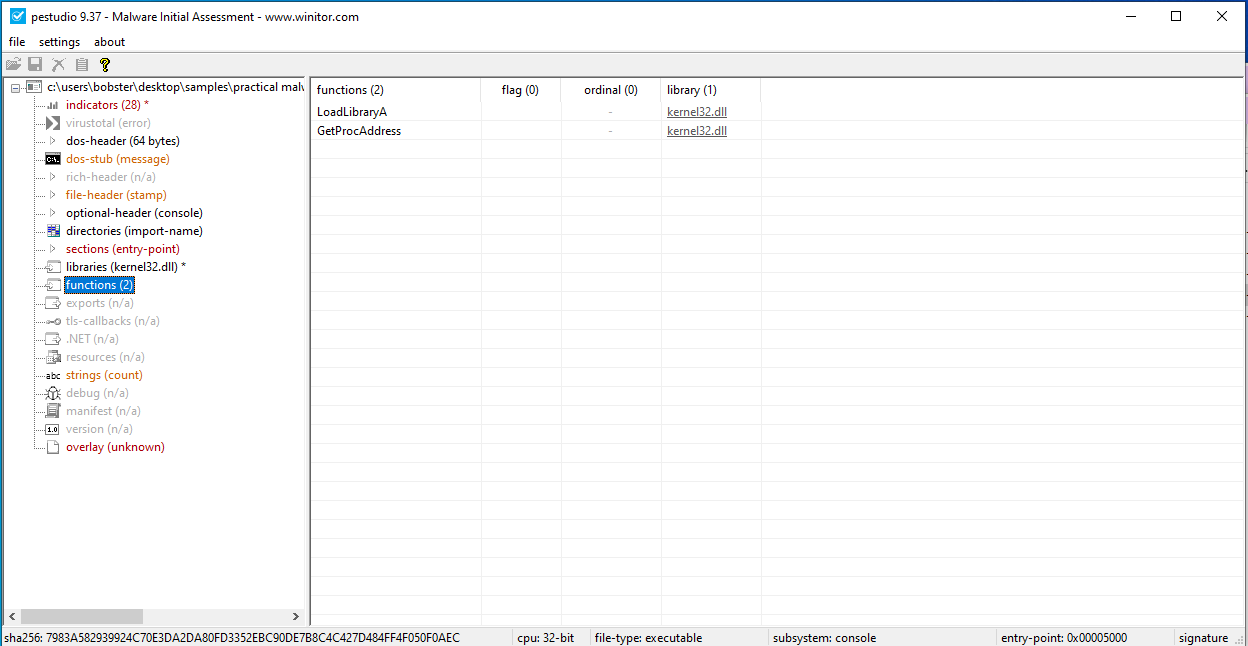
The above specified functions can cause other modules to be loaded during the calling process. But, with the information we have right now, we can’t say for certain which are those.
4.What host- or network-based indicators could be used to identify this malware on infected machines?
As of this moment, there aren’t any host- or network-based indicaters that we could use to identify this malware on infected machines.
Lab 1-4
- Upload the Lab01-04.exe file to http://www.VirusTotal.com/. Does it match any existing antivirus definitions?
Yes, it does.
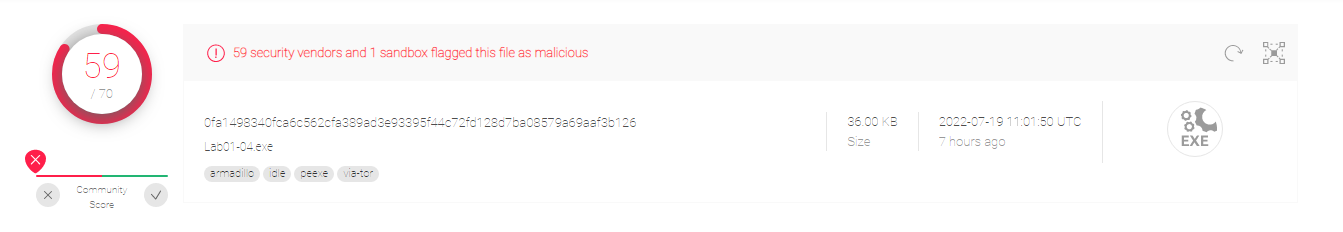
2.Are there any indications that this file is packed or obfuscated? If so, what are these indicators? If the file is packed, unpack it if possible.
The file is not packed, or obfuscated, as we can find a lot of strings and a lot of the files that are being used. All the sections, .text, .rdata, .data and .rsrc are visible. Using PEiD, we find out that it is compiled using Microsoft Visual C++ 6.0.
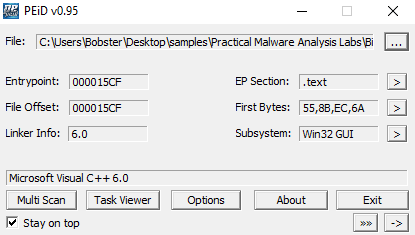
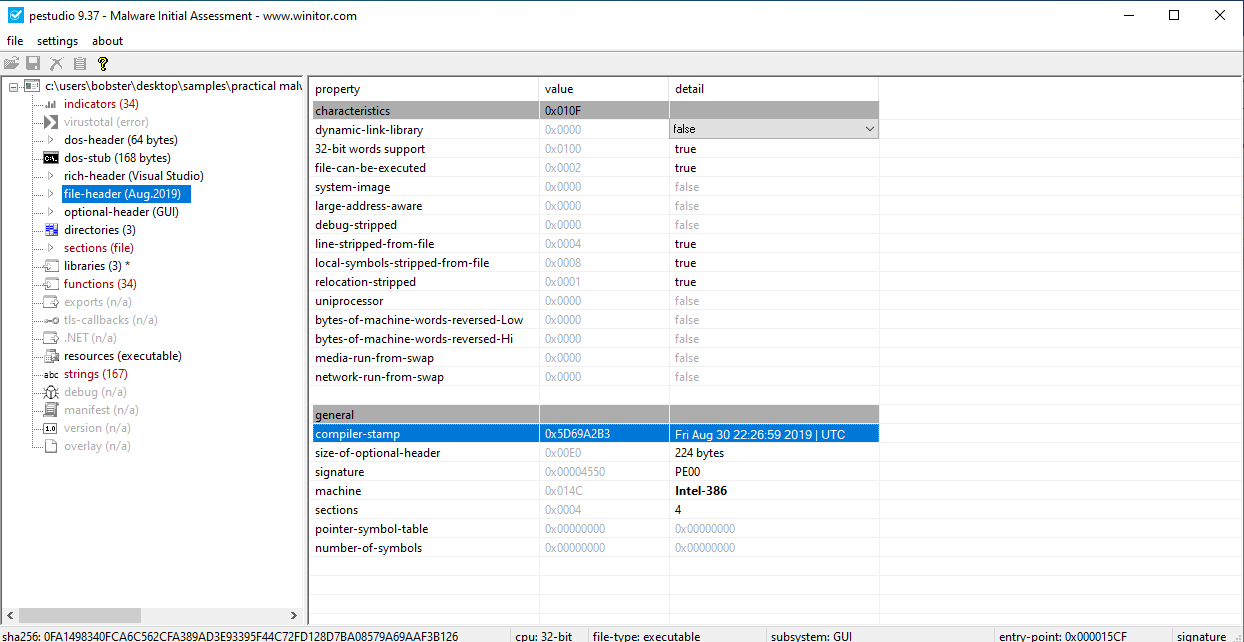
3.When was this program compiled?
| This program was compiled on Fri Aug 30 22:26:59 2019 | UTC. |
4.Do any imports hint at this program’s functionality? If so, which imports are they and what do they tell you?
Yes.
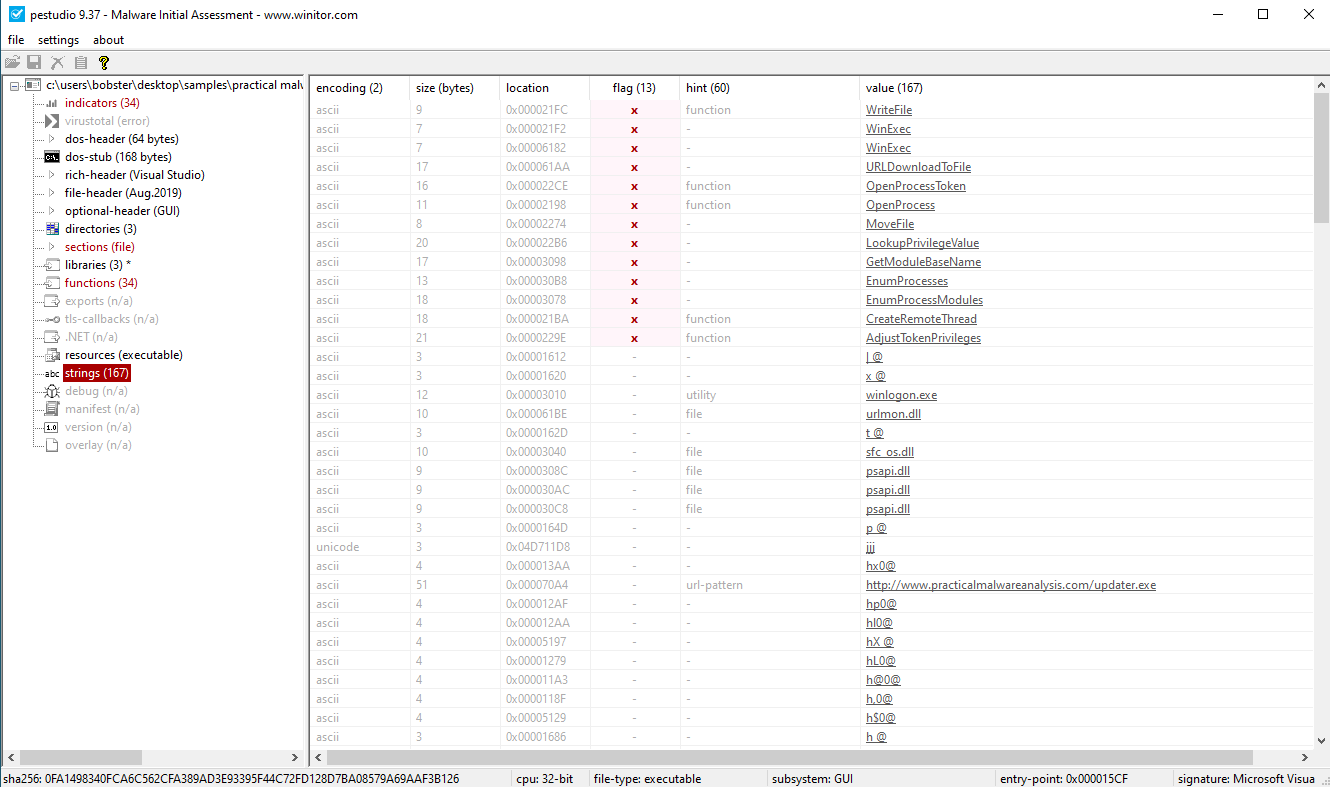
The malware may try to create the files \system32\wupdmgrd.exe, \system32\wupdmgr.exe, \system32\wupdmgr.exe,\winup.exe, to mimic Windows Update Manager. More than this, it will download another executable from http://www.practicalmalwareanalysis.com/updater.exe.
Also, it may use psapi.dll to look for process statuses and most likely maintain persistence. Also, sfc_os.dll is used to monitor system files for validity.
The LookupPrivelegeValue function is used to check the privilege level. Along with AdjustTokenPrivileges, it might try to change the privileges.
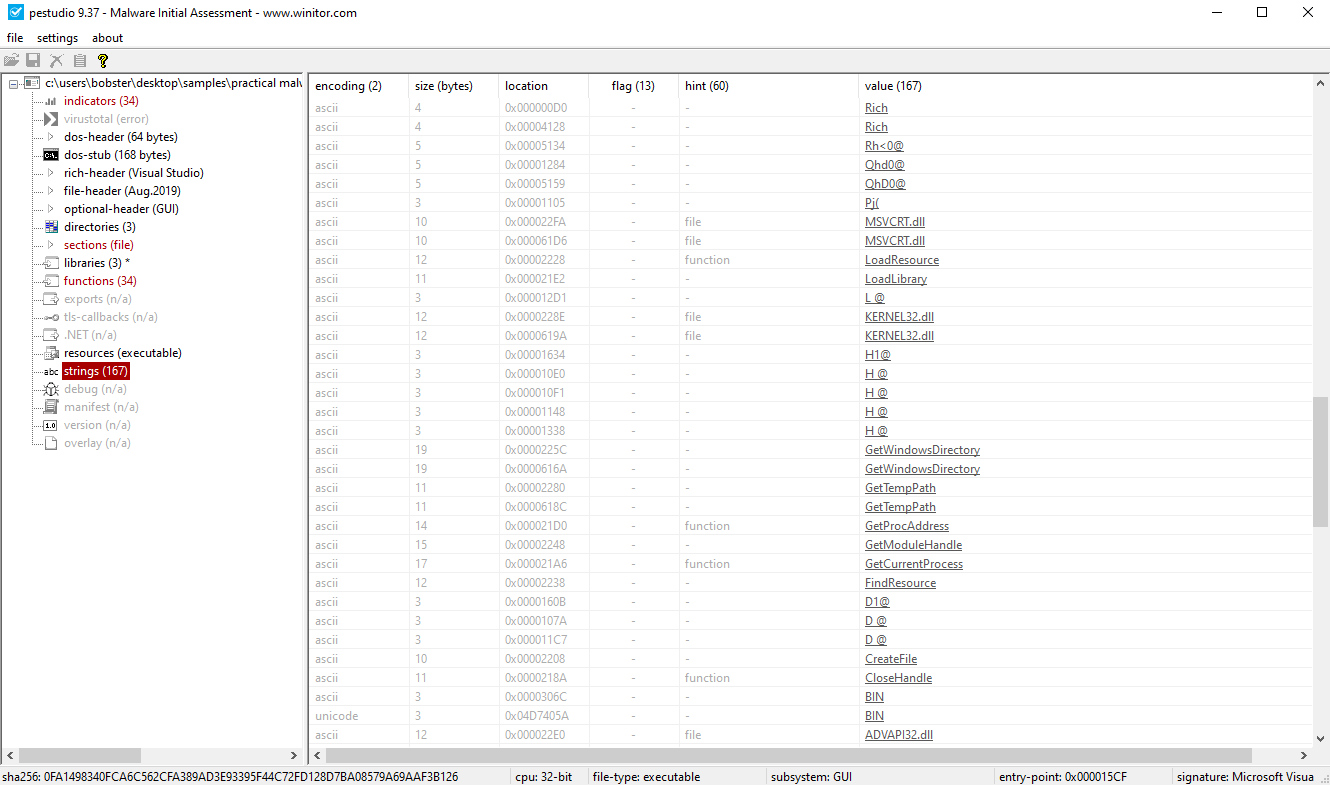
LoadResource and SizeofResource is used to load the resource found in the file.
5.What host- or network-based indicators could be used to identify this malware on infected machines?
The presence of the above mentiond executables and the connection to the URL can be indicators that could be used to identify this malware on infected machines.
6.This file has one resource in the resource section. Use Resource Hacker to examine that resource, and then use it to extract the resource. What can you learn from the resource?
The resource is an executable.
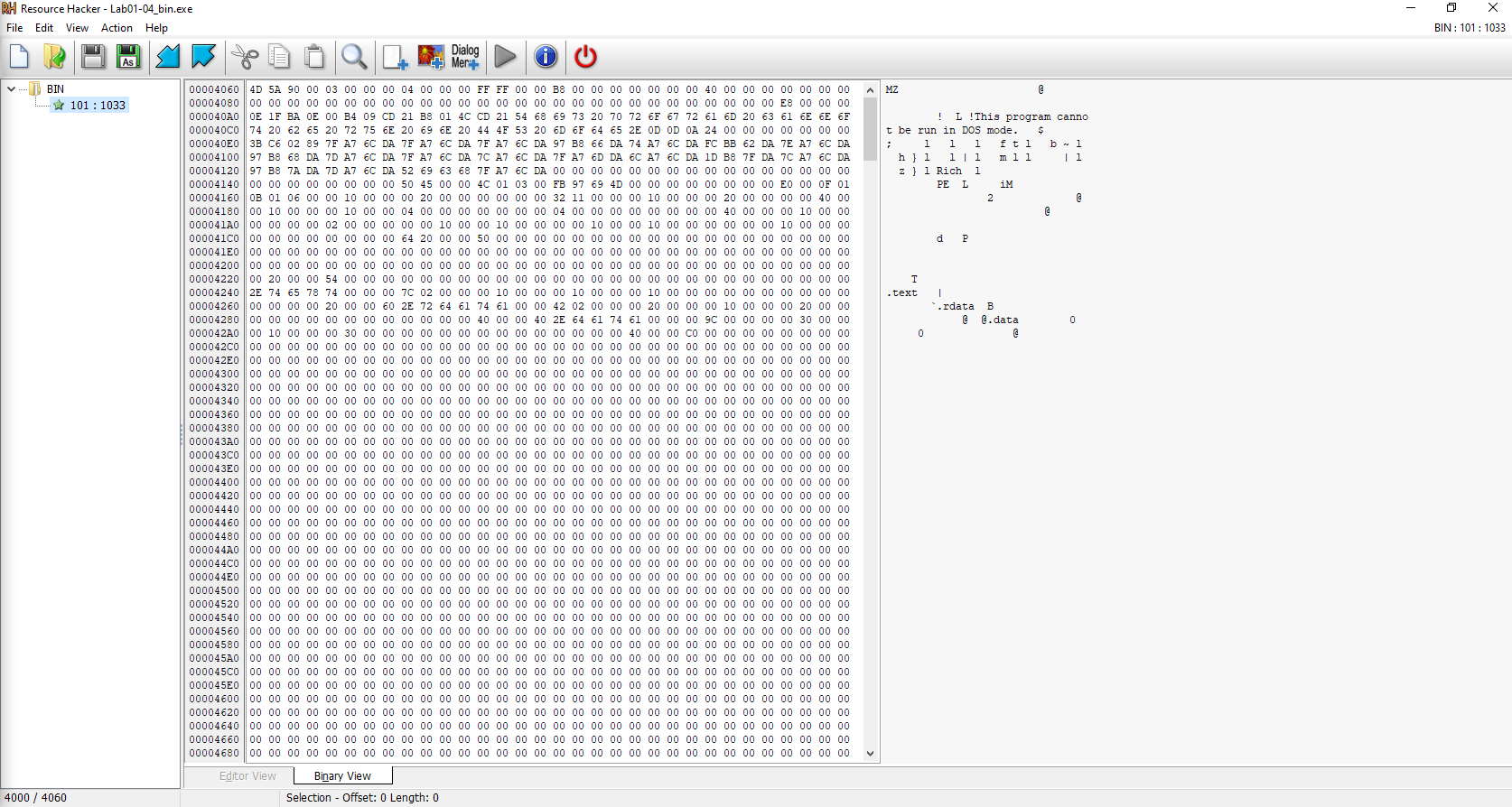
Using PEStudio we can observe that there we find the same strings as stated above. It also downloads and runs the updater.exe file.