Hello!
Welcome to the walkthrough of Chapter 3 - Labs.
Chapter 3
Lab 3-1
Analyze the malware found in the file Lab03-01.exe using basic dynamic analysis tools.
1.What are this malware’s imports and strings?
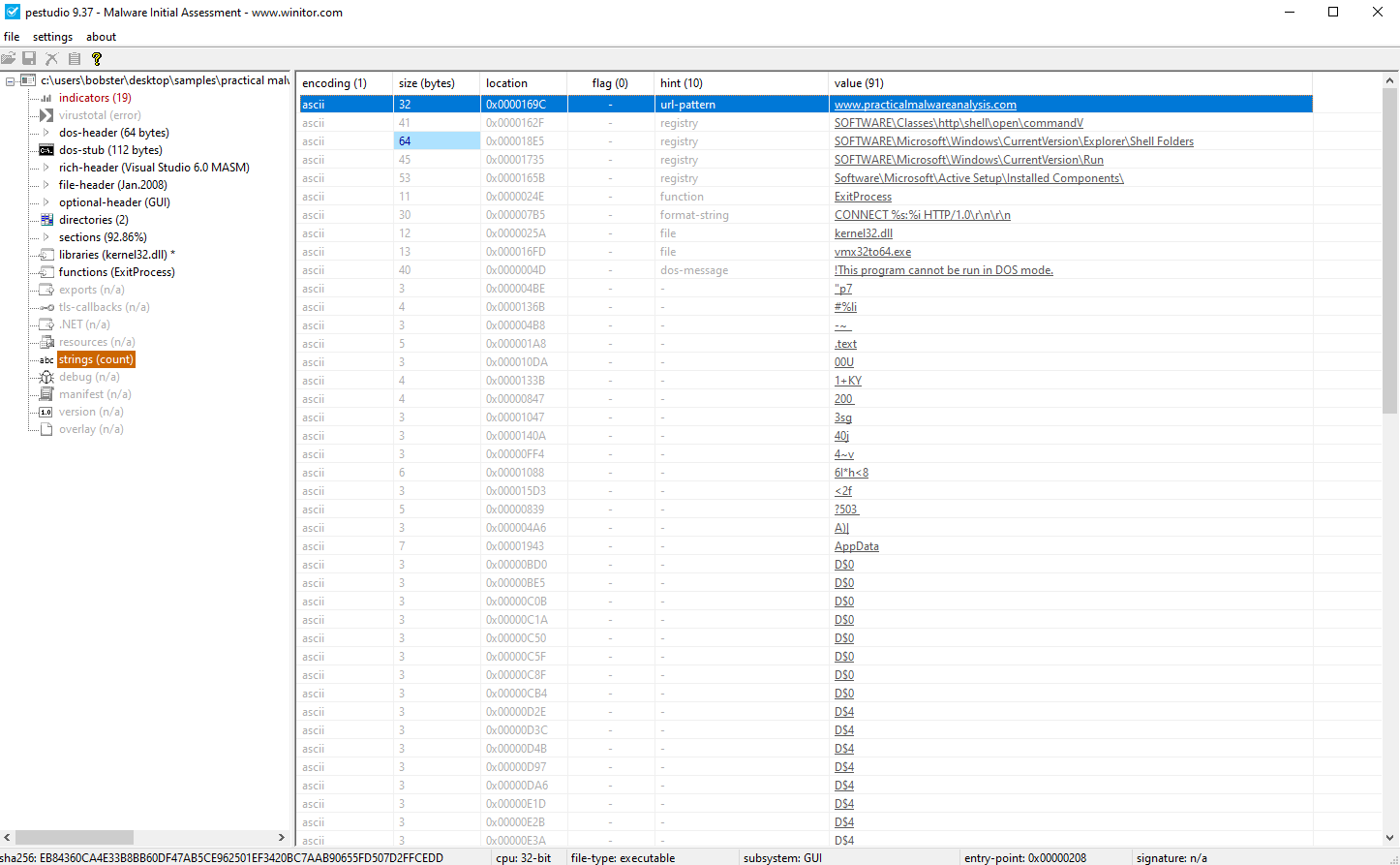
Using strings we found the following :
- An URL:
- www.practicalmalwareanalysis.com
- Registry keys:
- SOFTWARE\Classes\http\shell\open\commandV
- SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
- SOFTWARE\Microsoft\Windows\CurrentVersion\Run
- _Software\Microsoft\Active Setup\Installed Components_
- A CONNET HTTP Method:
- CONNECT %s:%i HTTP/1.0\r\n\r\n
- An executable file name:
- vmx32to64.exe
- Other strings:
- AppData
- StubPath
- advapi32
- advpack
- ntdll
As far as imports go, we can only find the function ExitProcess from the kernel32.dll library.
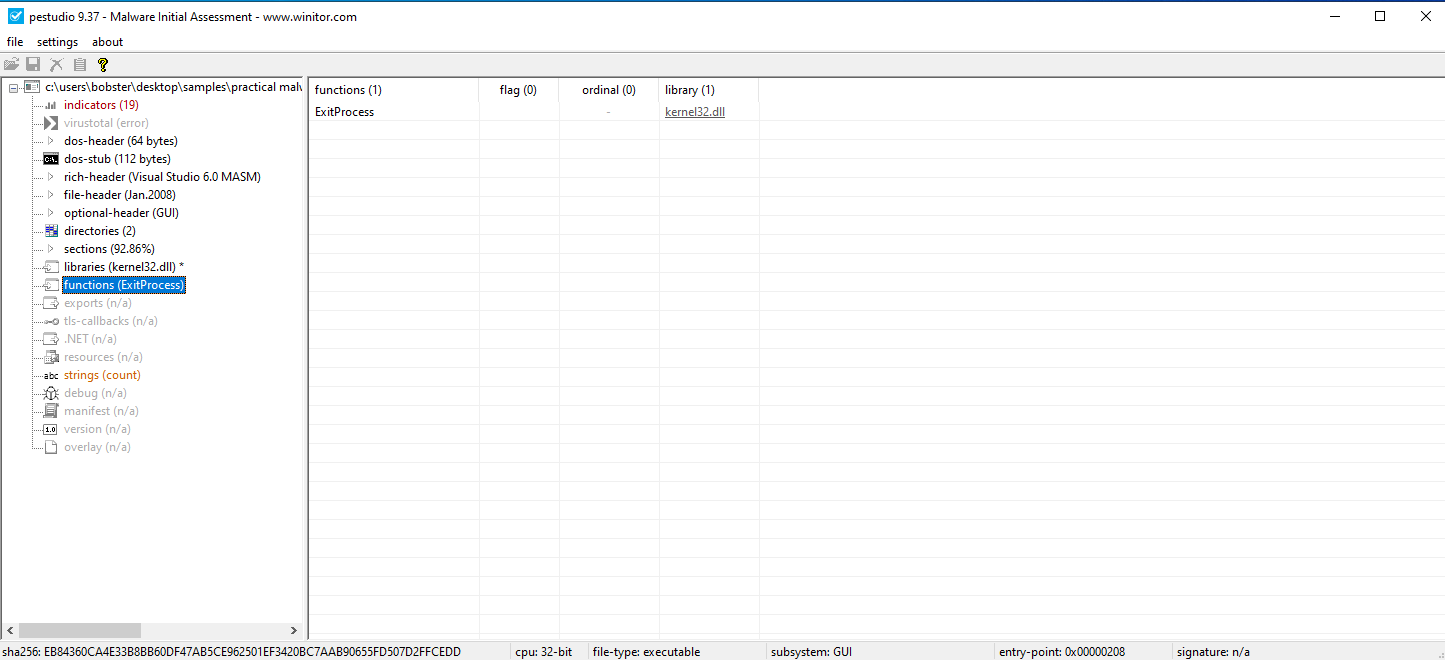
2.What are the malware’s host-based indicators?
Host-based indicators of this malware are the presence of the vmx32to64.exe file and modified registry keys.
3.Are there any useful network-based signatures for this malware? If so, what are they?
Yes, the network-based signature for this malware is the connection to the www.practicalmalwareanalysis.com URL .
#Lab 3-2
Now, for the analysis of the Lab03-02.dll things are a little bit different. Windows doesn’t know how to run .dll’s automatically, so we have to find a few commands in order to successfully launch it.
The syntax which we wil use is:
rundll32.exe DLLname, Export arguments
The Export value has to be a function name or an ordinal from the exported function table in the .dll. We can use PEStudio to view the Export table and, hopefully, find the value that we need.
As we can see in the following screenshot, a few functions are found :
- Install
- ServiceMain
- UninstallService
- installA
- uninstallA
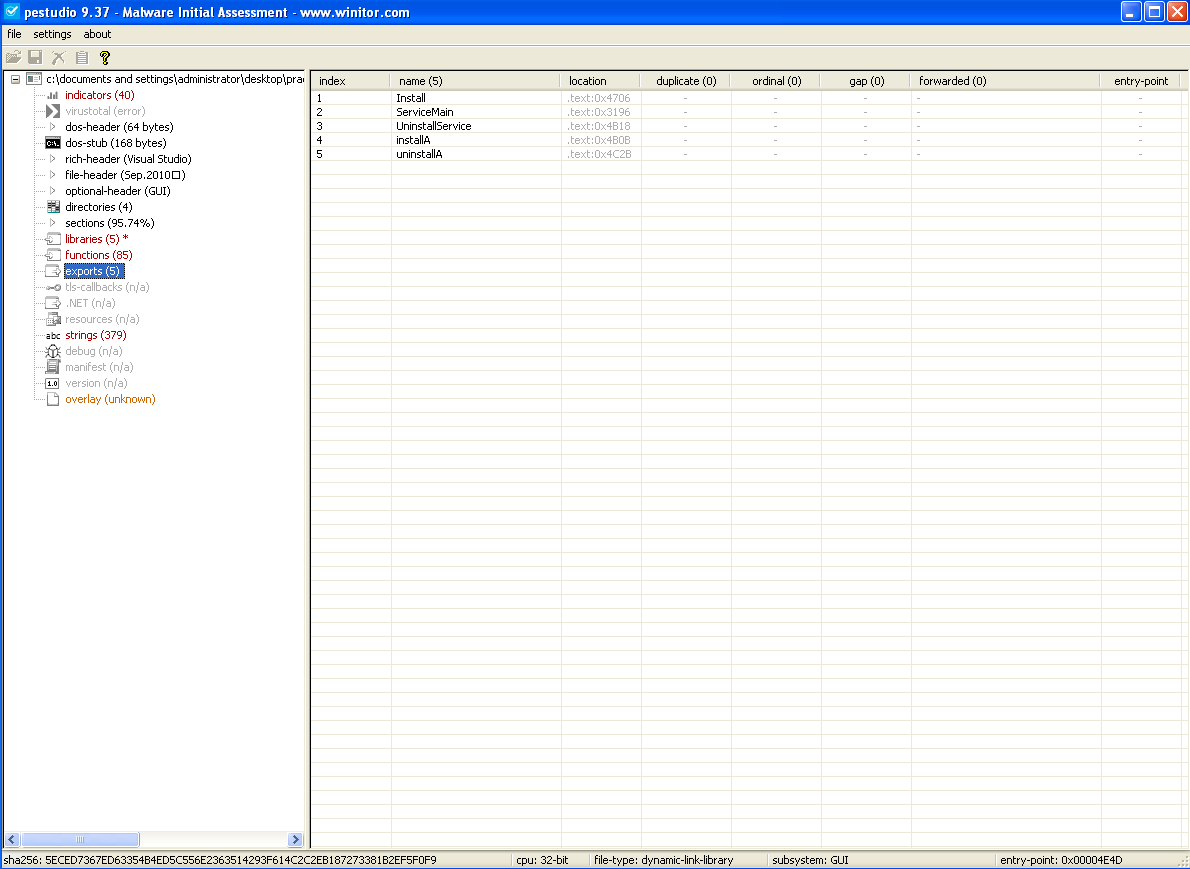
Install appears to be one that might render useful to us.
Now, let’s take a look at the strings in this sample to get a feeling about what this malware can do.
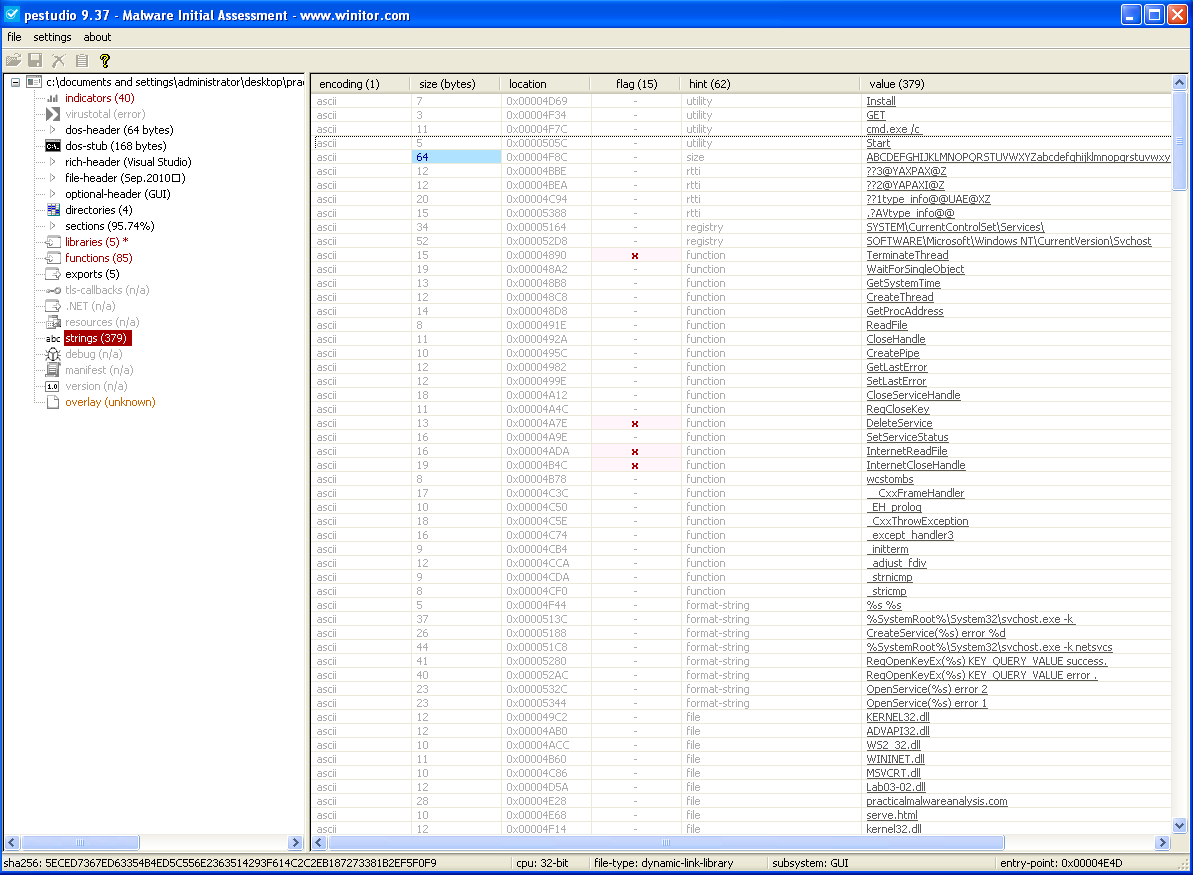
We can find a command to run cmd.exe, that is cmd.exe /c, using the /c flag in order to open a new shell, execute the provided command and exit the shell automatically.
There are also some Registry paths seen :
- _SYSTEM\CurrentControlSet\Services_
- SOFTWARE\Microsoft\Windows NT\CurrentVersion\Svchost
A network-based indicator can be seen :
- practicalmawlareanalysis.com
The presence of the file serve.html can be used as a host-based indicator.
The functions imported are from the kernel32.dll, advapi32.dll, ws232.dll, wininet.dll, msvcrt.dll libraries.
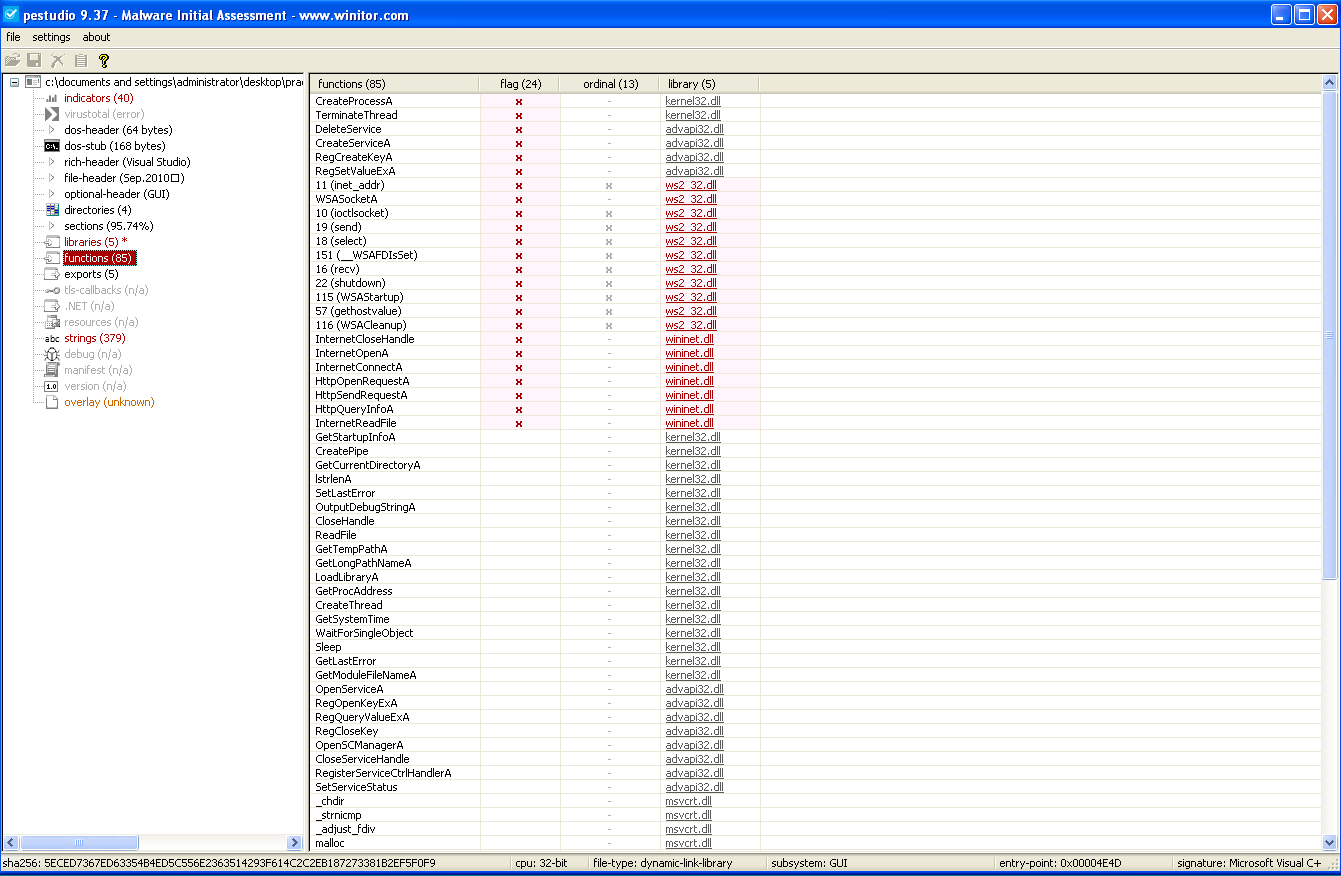
The socket functions lead us to think that it might try to connect to another machine. Also, with the HTTP and Internet functions, it’s clear that it will want to create different requests and open and read files from the internet. It will also read different files, execute some, start services and also use sleep probably as a way to not make so much noise on the machine.
Now, let’s get into some dynamic analysis.
First, let’s start:
- Process Explorer
- Process Hacker
- Process Monitor and exclude all the process that are not of need for us right now.
- Regshot, and take the 1st shot.
- Wireshark on the other machine.
- ApateDNS, INetSim
Once we are set up, let’s run the samples using the following command:
rundll32.exe Lab03-01.dll, Install
!!NOTE!! *Lab03-01.dll didnt’t launch as expected. The process is suspended once it launches. Some indicators and information may be missing from this analysis. *
Let’s first take a look at the following screenshots:
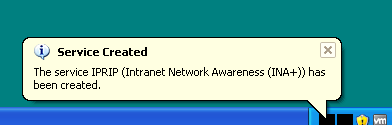
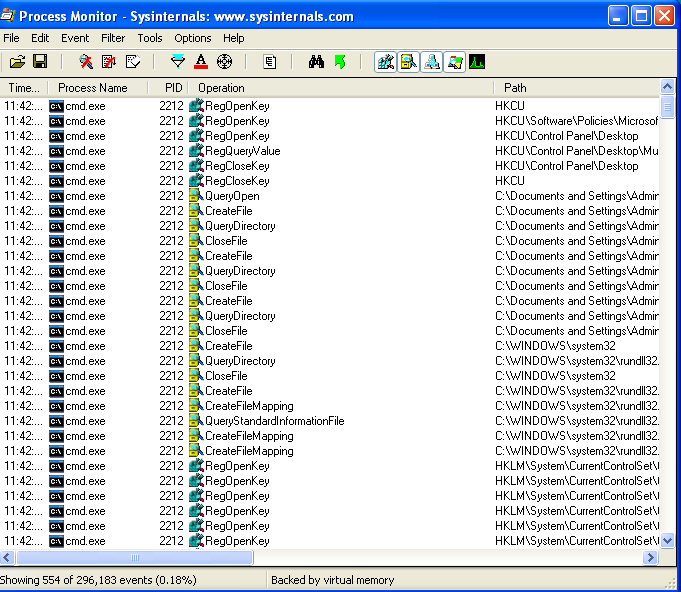
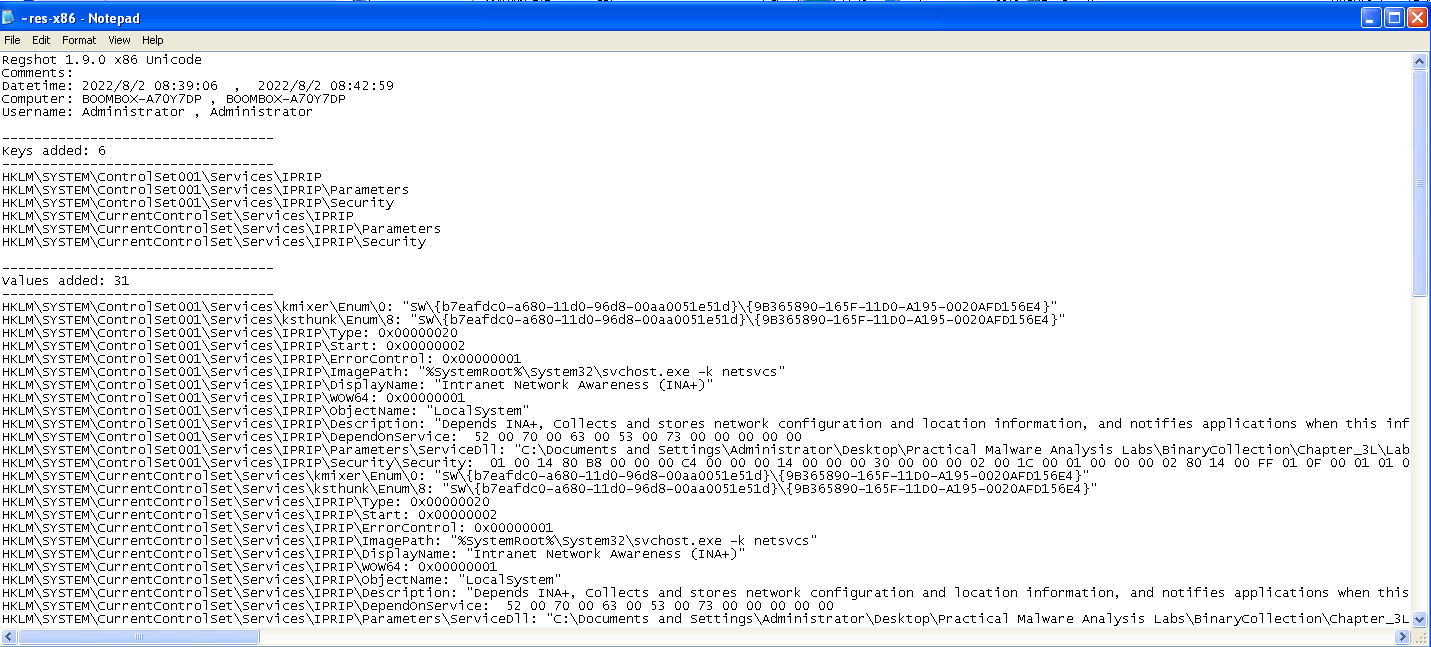
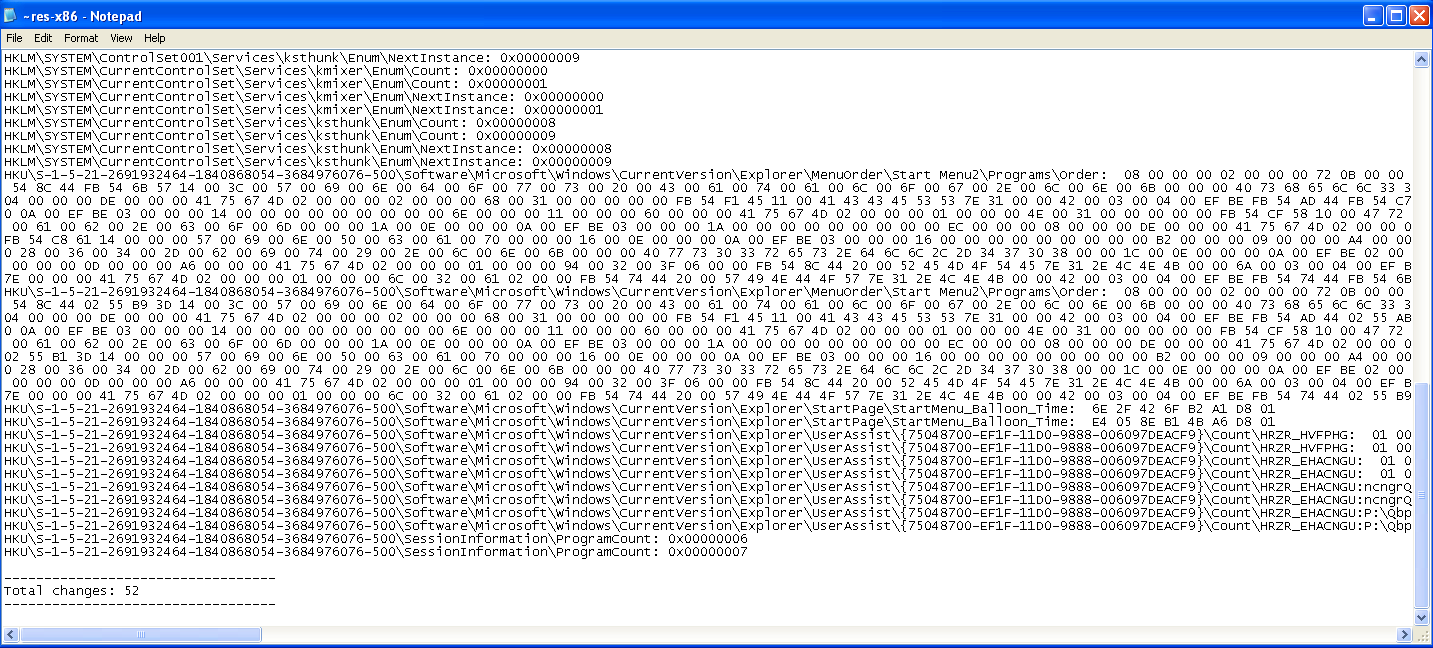
As we can see, a new service has been installed: IRPIP (Intranet Network Awareness (INA+)) . It’s, of course, a fake one.
With the use of ProcMon, we can see that 554 events have been created. Also, with RegShot we can see that it stores different values in the _HKLM\SYSTEM\CurrentrControlSet\Services\IPRIP_ registry, such as : the path of the sample, a command for svchost, different hex addresses and more. In total, there have been 52 changes to the registry made.
#Lab 3-3
Let’s run the same tools and launch the sample.
Upon monitoring this malware with Process Explorer, the sample runs for 2s, then quits.
#Lab 3-4
On Process Explorer and Process Hacker, there isn’t any activity shown. But, with ProcMon we can see what the sample did. The roadblock in dynamic analysis is caused by the fact that the malware might have some evasion tehniques in place which don’t let us analyze it further using dynamic analysis. After executing, the malware is deleted from the location.
The other way we can run this program is using a debugger.