Really good!! Let’s get familiar with C code constructs in Assembly.
Lab 06-01
In this lab, you will analyze the malware found in the file Lab06-01.exe.
Questions
1.What is the major code construct found in the only subroutine called by main?
The main function can be seen in Figure 1.1.
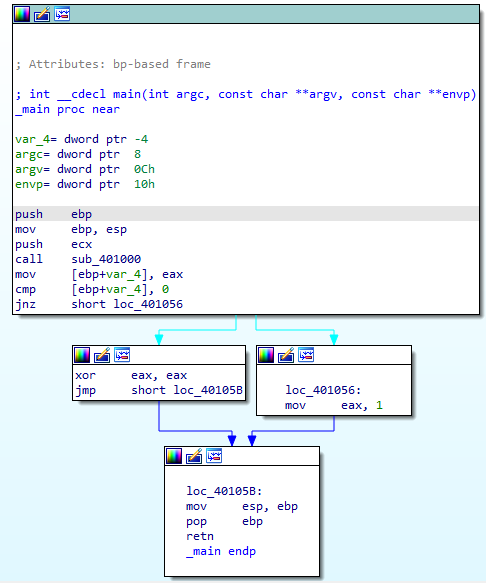
Figure 1.1
Now, let’s look into the subroutine, in Figure 1.2.
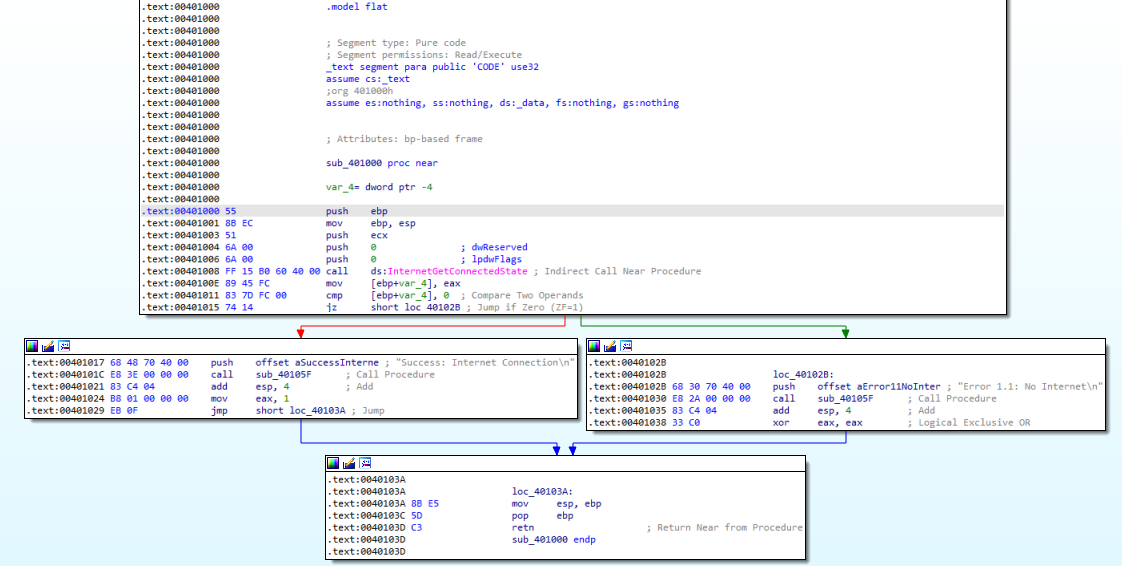
Figure 1.2
We can see that there is a call being made to the function InternetGetConnectedState. The program checks for an internet connection.
At 0x401015 a conditional jump is made. If the condition is met, a string will most likely print on the screen, saying that there is no internet connection. On the other side, another message stating that there is a connection will pop up on the screen.
The major code construct found in the only subroutine called by main is an if statement.
2.What is the subroutine located at 0x40105F?
The block of code can be seen in Figure 2.1.
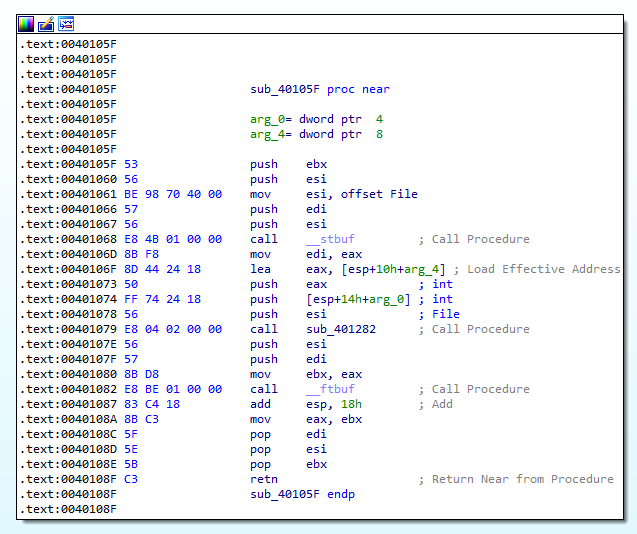
Figure 2.1
Taking into consideration that the subroutine is called in the if statement right after a string being pushed to the stack, we can assume that the subroutine located at 0x40105f is a printf statement.
3.What is the purpose of this program?
The purpose of this program is to check for an internet conection. If it exists, a message will be printed on screen regarding the result.
Lab06-02
Analyze the malware found in the file Lab06-02.exe.
Questions 1.What operation does the first subroutine called by main perform?
The first subroutine called by main is the one analyzed before. It performs an if statement to check if an internet connection exists.
2.What is the subroutine located at 0x40117F?
The subroutine located at 0x40117F is the printf function. We can now rename it.
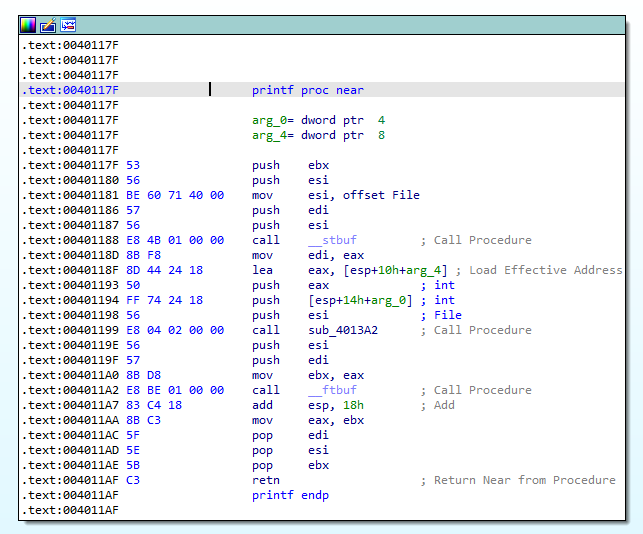
Figure 2.1
3.What does the second subroutine called by main do?
The second subroutine opens an internet connection and tries to download the page at http://www.practicalmalwareanalysis.com/cc.htm .
4.What type of code construct is used in this subroutine?
In this subroutine, the if statement is used. Also, checking the microsoft documentation regarding the InternetReadFile function, we can assume that the buffer variable is an array.
5.Are there any network-based indicators for this program?
Yes, the network-based indicator for this program is the URL http://www.practicalmalwareanalysis.com/cc.htm
6.What is the purpose of this malware?
It firstly checks for an internet connection. Then, using the subroutine 401040, it opens an internet connection in order to read a file from the practicalmalwareanalysis URL. Then, it tries to read a string from the html file, character by character. If it finds the string “<!- -“(without the space in between the dashes) then, the program will print a “success:parsed command is X “, string.
After this, the value 60.000 is pushed on to the stack before the Sleep function to make the program sleep for 60s.
Lab 06-03
Questions
1.Compare the calls in main to Lab 6-2’s main method. What is the new function called from main?
The subroutines at 0x401000 and at 0x401271 (printf) are the same as the ones in Lab 06-02. The new function is at 0x401130.
2.What parameters does this new function take?
As seen in Figure 2.1, this function takes a character and the argv argument from the main function as parameters.
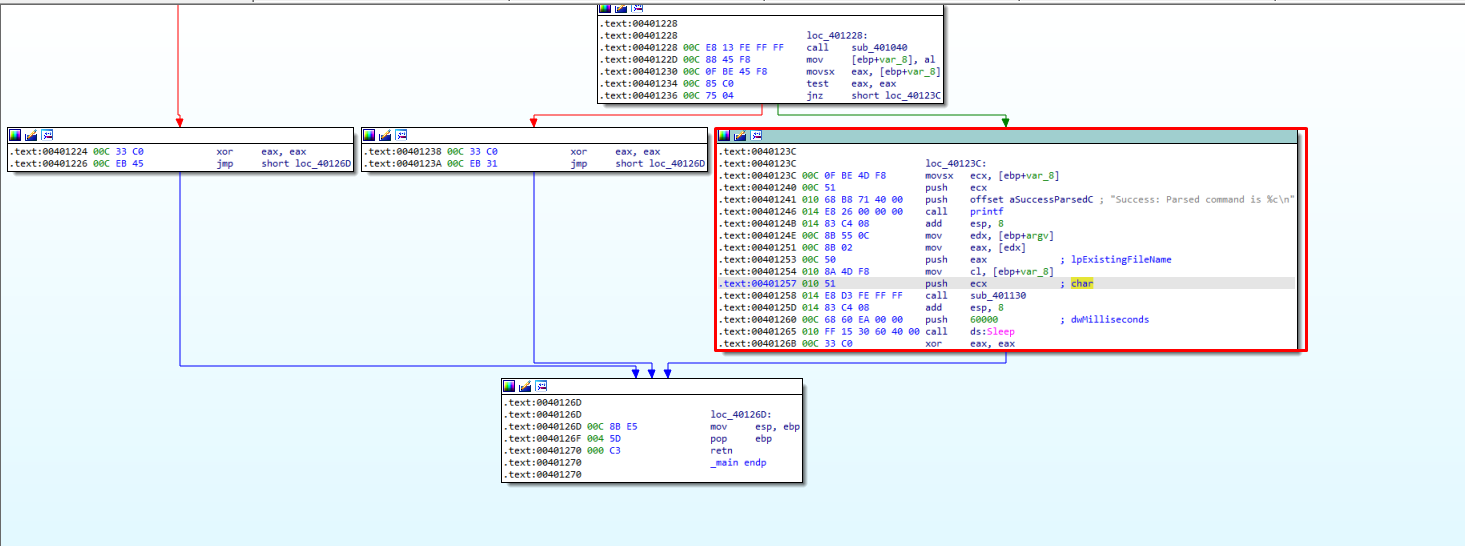
Figure 2.1
3.What major code construct does this function contain?
This function contains a switch statement, as seen in Figure 3.1.
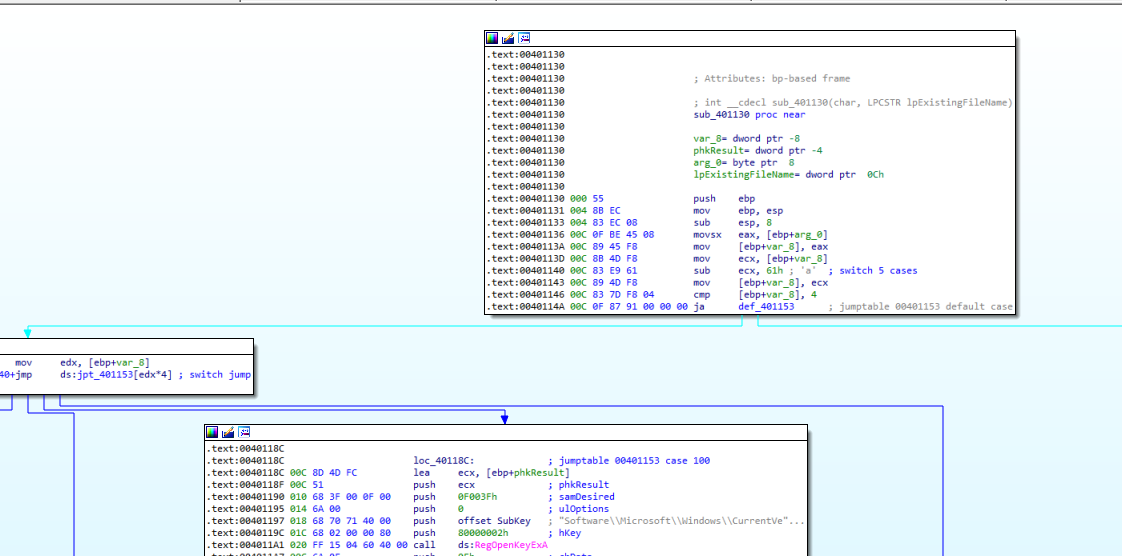
Figure 3.1
4.What can this function do?
This function can:
- Create a new directory, C:\Temp. (Figure 4.1)
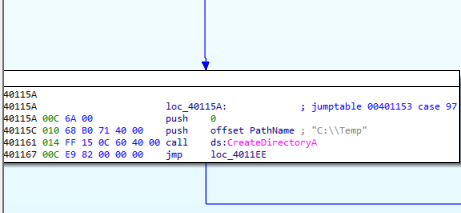
Figure 4.1
- Copy one or more files from a location to another, as seen in Figure 4.2.
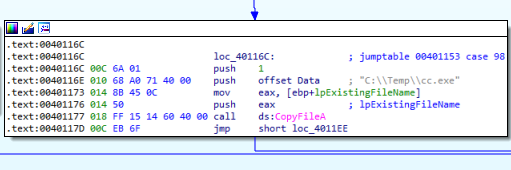
Figure 4.2
- Delete a file. (Figure 4.3)
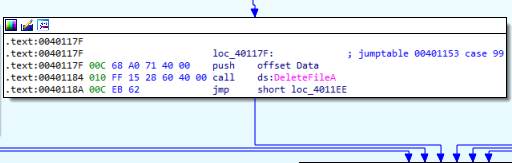
Figure 4.3
- Sleep for 100s (186A0h_ms). (Figure 4.4)
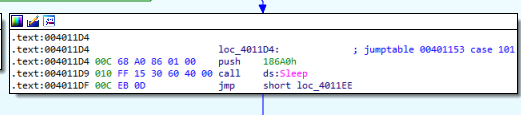
Figure 4.4
- Print an error message. (Figure 4.5)
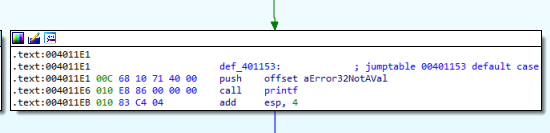
Figure 4.5
- Set a new registry value. (Figure 4.6)
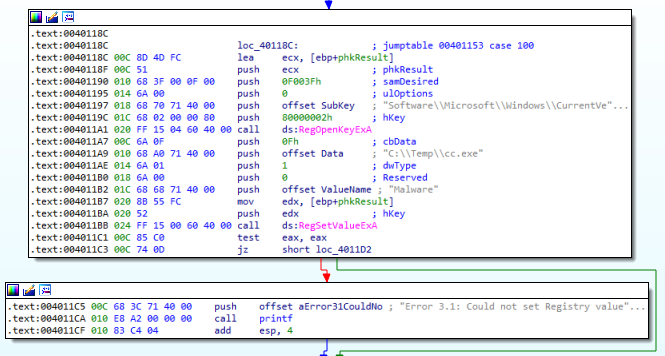
Figure 4.6
5.Are there any host-based indicators for this malware?
Host-based indicators for this malware are the registry key “Software\Microsoft\Windows\CurrentVersion\Run\Malware” and the file location “C:\Temp\cc.exe”.
6.What is the purpose of this malware?
This malware firstly checks for an Internet connection. If there is no such connection, the program terminates. Otherwise, it will try to access a web page that contains a custom HTML comment beggining with “<!- -“. The first character is passed in a switch statement to determine what step to take next. That includes all the possibilities from Question 6.
Lab 06-04
1.What is the difference between the calls made from the main method in Labs 6-3 and 6-4?
As seen in Figure 1.1, this sample also has the printf function, switch statement and the check for internet connection function.
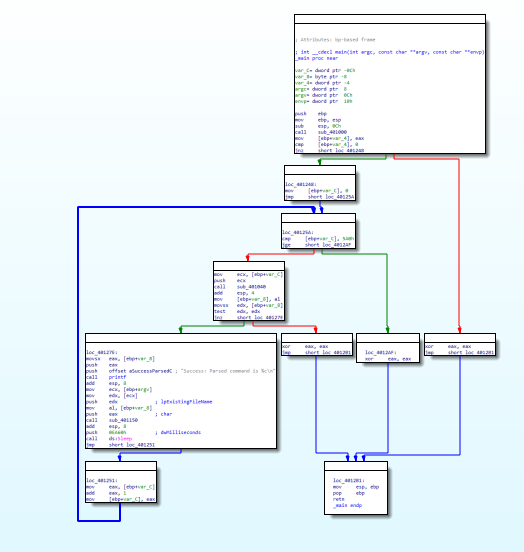
Figure 1.1
2.What new code construct has been added to main?
A for loop has been added to the main function.
3.What is the difference between this lab’s parse HTML function and those of the previous labs?
The code construct can be seen in Figure 3.1.
Compared to the previous lab, an User-Agent is used for the internet connection. (Internet Explorer 7.50/pma%d).
4.How long will this program run? (Assume that it is connected to the Internet.)
The var_c represents the incerementor for the for loop. It ends at the value 1440. Observing that inside the loop, the program will sleep for 60000ms, 60s, 1min, we can definetly say that the program will run for 1440 * 1min=1440min .
5.Are there any new network-based indicators for this malware?
Yes, the network-based indicators are the visited website, http://www.practicalmalwareanalysis.com/cc.htm and the User-Agent used, Internet Explorer 7.50/pma%d.
6.What is the purpose of this malware?
Firstly, the malware checks for an internet connection. If it is not found, the malware terminates. If it does exist, the sample will use a custom-made User-Agent in order to download a web page. The next steps are the same ones as the ones in the last exercise. Furthermore, this sample will only execute for 1440mins.